Raspberry Pi SSH: Firewall Setup Guide
Want to control your Raspberry Pi from anywhere in the world? Secure Shell (SSH) is the key, offering a powerful and versatile way to manage your Pi remotely, even when it's tucked safely behind a firewall.
Accessing a Raspberry Pi remotely opens a world of possibilities. Imagine managing files, running scripts, and controlling applications without ever needing to be physically near the device. SSH makes this a reality, providing a secure encrypted connection over your network or the internet. But navigating firewalls can be tricky. This deep dive explores the nuances of SSH and firewalls, providing a comprehensive guide for securely accessing your Raspberry Pi from a Windows machine.
| Topic | Raspberry Pi SSH Access Through Firewalls |
| Key Technologies | SSH, Firewalls, Port Forwarding, Tunneling, Raspberry Pi OS, Windows |
| Benefits | Remote management, secure access, increased flexibility, enhanced control |
| Reference | Raspberry Pi Official Documentation |
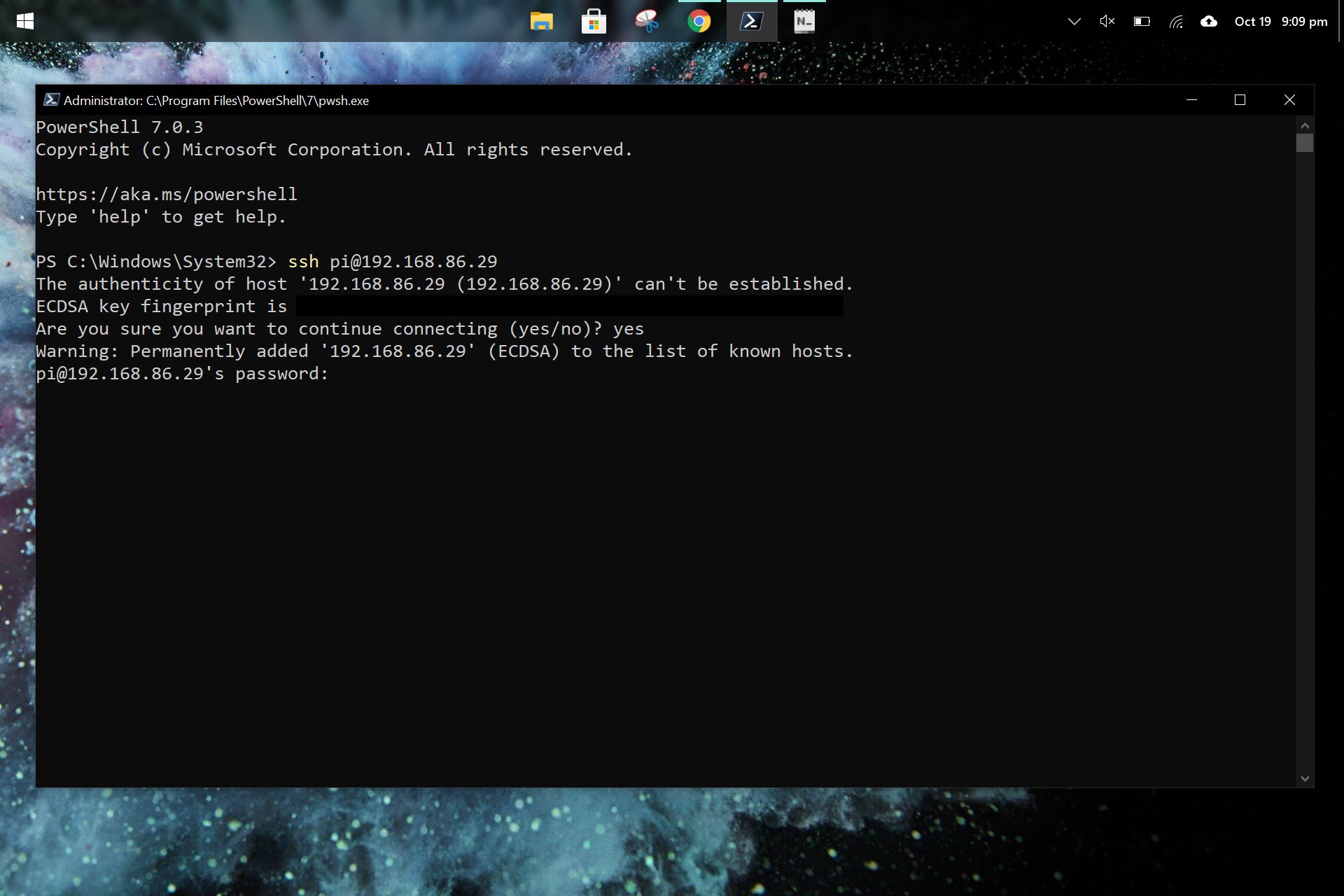
The first step in this journey involves enabling SSH on your Raspberry Pi. If you have a display connected, simply navigate to `Preferences > Raspberry Pi Configuration > Interfaces` and enable SSH. For headless setups (without a monitor), editing the `ssh` file in the `boot` partition on the SD card will activate SSH. This ensures the SSH server is running and ready to accept connections.
- Tyra Banks Erik Asla Relationship Timeline Everything You Need To Know
- Jillian Mele Age Birthday Facts You Need To Know
Knowing your Raspberry Pi's IP address is crucial for remote access. While straightforward on a local network, things get more complex when firewalls are involved. Tools like `ipconfig` (Windows) or `ifconfig` (Linux/macOS) can reveal the local IP, but for external access, your routers public IP is needed. Services like Tailscale can simplify this process, creating virtual networks that bypass complex firewall configurations, enabling access as if your Pi were on your local network.
Copying files between your computer and your Raspberry Pi becomes a breeze with SSH. From the directory containing the file on your computer, a simple command like `scp myfile.txt username@raspberry_pi_ip_address:~/` will securely transfer `myfile.txt` to your Pi's home directory. Just replace the placeholders with your Pi's username and IP address.
Firewalls are essential security tools, acting as gatekeepers for your network. They control incoming and outgoing traffic, protecting your devices from unauthorized access. By configuring firewall rules, you can specify which ports and services are accessible, minimizing vulnerabilities. On your Raspberry Pi, `ufw` (Uncomplicated Firewall) offers a user-friendly interface for managing these rules. For instance, `sudo ufw limit 22` restricts the number of SSH connection attempts, bolstering security against brute-force attacks.
Port forwarding is another crucial technique. It directs traffic arriving at your router on a specific port to a particular device and port on your internal network. By forwarding port 22 (the default SSH port) on your router to your Raspberry Pi's IP address, you effectively open a secure channel for external SSH connections. While the process varies depending on your router model, it typically involves accessing your router's configuration page and setting up a port forwarding rule.
SSH tunneling, facilitated by tools like `sshuttle`, provides an alternative method for bypassing firewall restrictions. It creates a secure tunnel between your computer and the Raspberry Pi, allowing you to access the entire Pi network as if you were connected locally. This method is particularly useful for accessing services running on ports other than 22.
When your Raspberry Pi is behind a firewall on a Windows network, several approaches can be employed. Enabling the SSH client on Windows 10, using command-line tools like `ssh` from PowerShell or Command Prompt, and configuring firewall rules to allow outbound SSH connections are essential steps. If direct SSH access proves problematic, tools like ngrok or PageKite can create secure tunnels, bridging the gap through their servers and bypassing the firewall altogether. These tools are particularly useful when dealing with dynamic public IP addresses or restrictive network configurations.
Troubleshooting SSH connections can be a challenge. Common issues include incorrect IP addresses, disabled SSH servers, or firewall restrictions. Carefully checking your Pi's IP, ensuring SSH is enabled, verifying firewall rules, and trying alternative methods like tunneling or hostname resolution can help pinpoint the problem. If connecting from a Windows machine, ensure the SSH client is enabled and that firewall rules allow outbound connections on port 22. If using a wired and wireless connection simultaneously, network routing conflicts might arise. Ensuring only one active interface can resolve these issues.
Mastering SSH access through firewalls empowers you with complete control over your Raspberry Pi, regardless of location. From managing files and running scripts to deploying applications and controlling hardware, the possibilities are vast. By understanding the intricacies of firewalls, port forwarding, and tunneling, you can confidently and securely access your Pi, unlocking its full potential as a versatile and powerful computing platform.
Detail Author:
- Name : Dr. Gavin Osinski III
- Username : jodie.jones
- Email : abshire.adam@frami.com
- Birthdate : 1991-06-13
- Address : 38982 Rau Burg Apt. 836 Lake Aylinshire, IL 79865
- Phone : 727-229-5761
- Company : Lubowitz-Zulauf
- Job : Actuary
- Bio : Repellat aut tenetur magnam quis consequatur aut et. Qui nisi et hic quam saepe quos. Quo dolorem sunt quis assumenda id blanditiis.
Socials
twitter:
- url : https://twitter.com/obeier
- username : obeier
- bio : Rerum assumenda consectetur vel aliquam nesciunt occaecati. Voluptates delectus est illo. Reiciendis quis eum distinctio nulla doloremque voluptates molestiae.
- followers : 469
- following : 2441
facebook:
- url : https://facebook.com/odie.beier
- username : odie.beier
- bio : Quia voluptatibus non voluptatem qui. Aut reprehenderit sunt aut voluptas.
- followers : 381
- following : 134
linkedin:
- url : https://linkedin.com/in/odie_beier
- username : odie_beier
- bio : Et ut in corporis aspernatur provident.
- followers : 837
- following : 1889